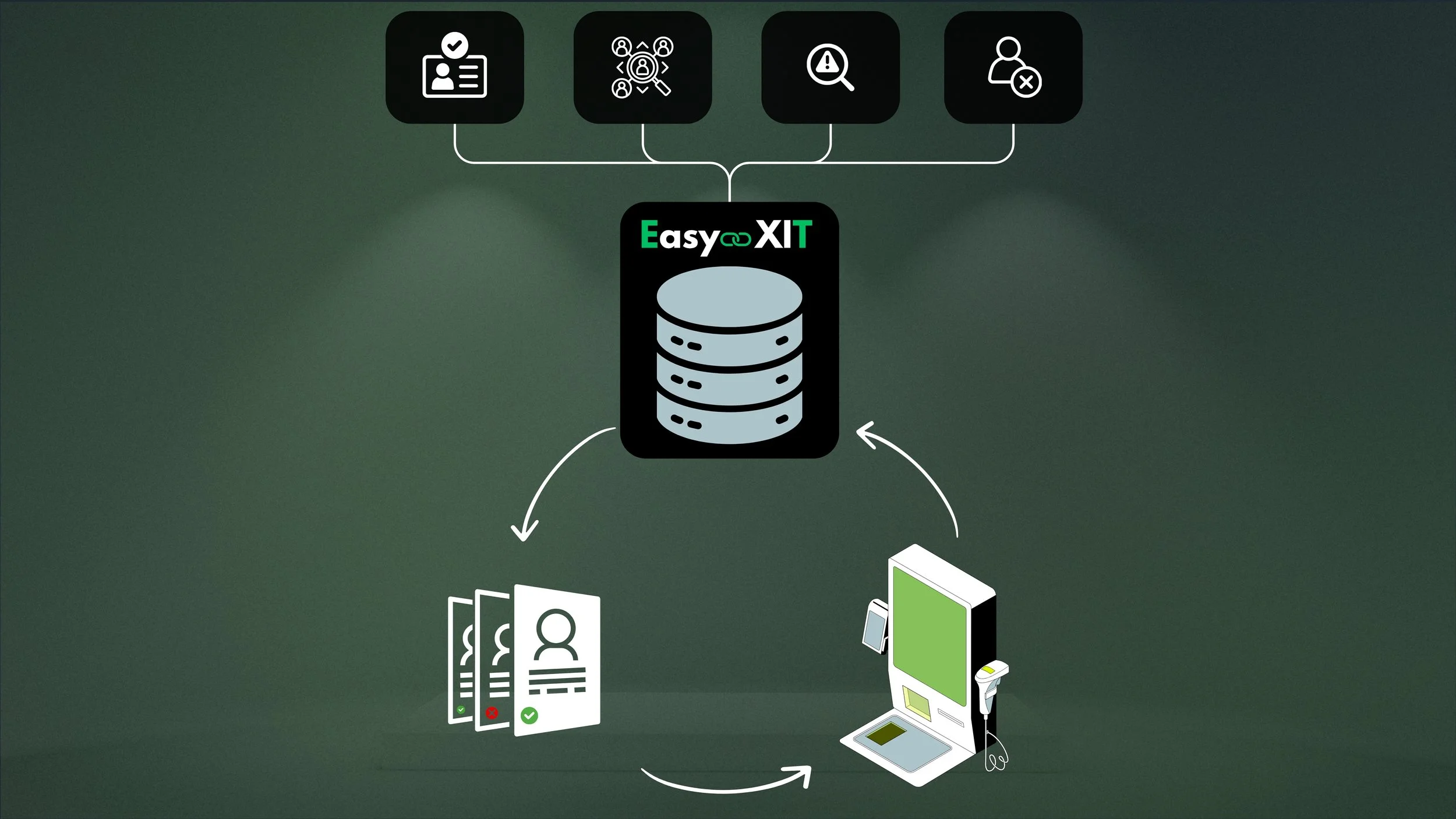
How It Works
To understand the solution, you must understand the problem.
The Problem
<10BSEK Total Value of Theft in 2023, Swedish Retail Alone
Rationalization
The anonymity of self-checkouts makes it easier for customers to justify not scanning items. Without face-to-face interaction, guilt fades, and theft feels less significant.
70% of all thefts occurs in self checkouts
Customer Anonymity
Many self-checkout users aren't identified, making it hard to track theft and hold individuals accountable. This anonymity encourage dishonest behavior.
Pressure on Staff
Determining intent at self-checkout is difficult. This puts pressure on staff and can discourage them from intervening, allowing theft to go unchecked.
Even when a spot-check reveals that a customer has missed scanning items, effective measures can only be taken if it’s clear the act was intentional. However, in most cases, it’s unclear, leaving staff in the uncomfortable position of deciding whether it was intentional or not. This creates unnecessary tension and puts staff in a psychologically unsafe situation, making theft prevention even more challenging.
The Challenge of Unclear Intentions
The Excuse
“I’m sorry, I made a mistake.” Most customers say this during a spot-check, leaving staff to decide if it was intentional or not. This responsibility shouldn’t fall on the staff—it should be managed by the system for fairness and consistency.
The Solution by EasyXIT
We tackle the problem head-on. By integrating with your POS, we enforce mandatory identification, create customer profiles, and log fraudulent behavior. These profiles are shared across all connected stores, forming a unified security network—working together to eliminate theft in self-checkouts.
Step 1: Mandatory Identification
It starts with requiring customer identification through secure methods like BankID or its equivalents, ensuring that every transaction begins with trust and accountability. EasyXit hosts and manages these identification methods, eliminating any extra burden on the POS provider.
Step 2: Customer Profile
EasyXit uses identification to track security-related events for self-checkout users when necessary. This serves as the foundation for generating alerts, warnings, and temporary blocks. Best of all, by integrating with various stores and POS systems, every store gains access to the same security insights—without storing unnecessary personal data.
Step 3: Automated Warnings
Automated warnings take the responsibility off staff, allowing them to empathize with customers instead of making tough judgment calls. If a spot-check reveals a discrepancy, a warning is instantly logged in the customer profile. This helps retailers track behavior, improve decisions, and reduce theft risks across the network.
Step 4: Industry-Wide
We connect retailers through a shared security system. When a fraud-prone customer uses a self-checkout at any system we integrate with, the system instantly identifies the risk and adjusts accordingly. This industry-wide approach creates a unified front against theft, protecting all participating retailers.
Contact us
Ready to collaborate? Share your details, and we’ll get back to you soon.
Mail us at: contact@easyxit.com